This week, @OverflOw from Zero 2 Automated course gave us a new challenge. The goal this time is to unpack a sample, find and reverse its string decryption routine and produce a script that will write them into our disassembler.
Unpacking
Bad news, the sample is packed with a .NET layer. I already hate .NET when I have to analyse code but I think i can’t analyse a .NET packer at the moment. I will need more knowledge (and patience) about this language and its tools.
So I decided to go completely lazy and unpack it automatically using the amazing unpac.me tool.
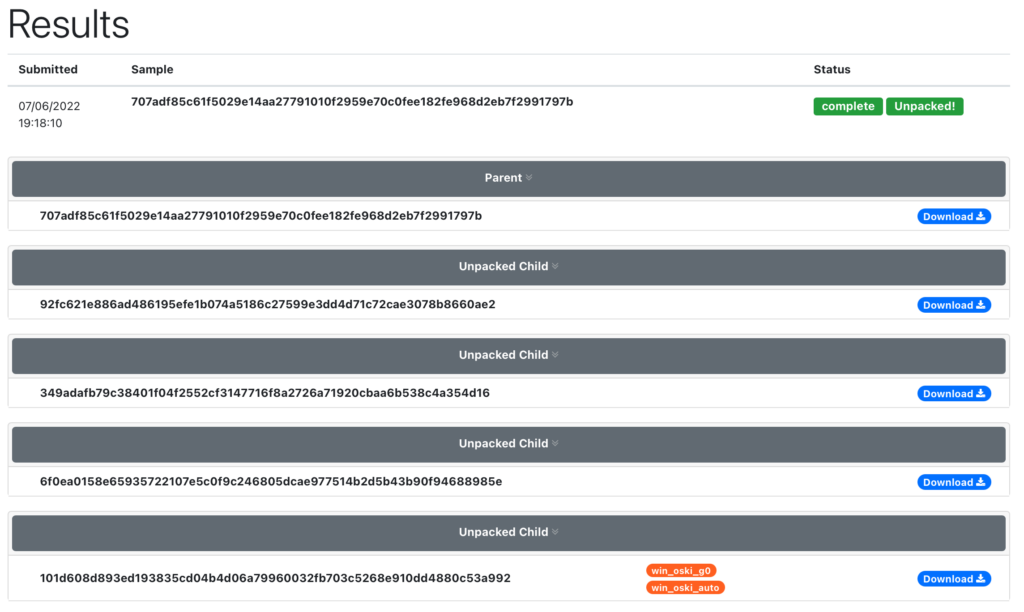
As we can see, the packer contains 4 different layers of code that leads to our unpacked binary.
I normally prefer unpack malwares myself, but in this case, I would have lost a lot of time unpacking it.
String decryption
When opened in IDA, the sample ends on a “start” function. This function is part of a binary who uses WinMain. This is easy to find main function in this kind of programs.
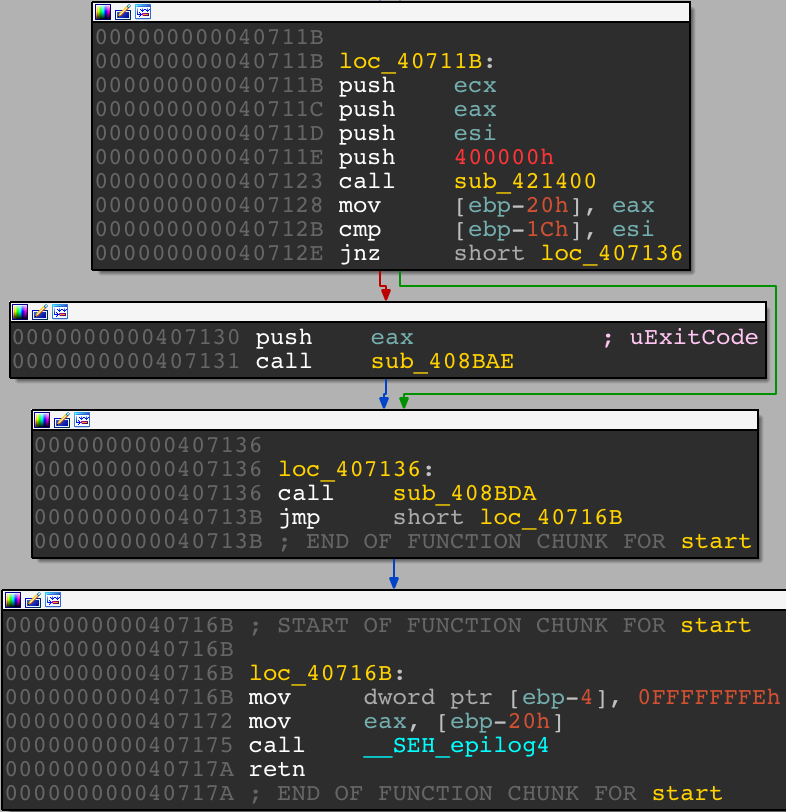
Look for this 400000h and the main function must be right after ;)
The very first function in this program is the string decryption one.
We can see a lot of calls to one function which will push sort of encrypted data and return something else in eax.
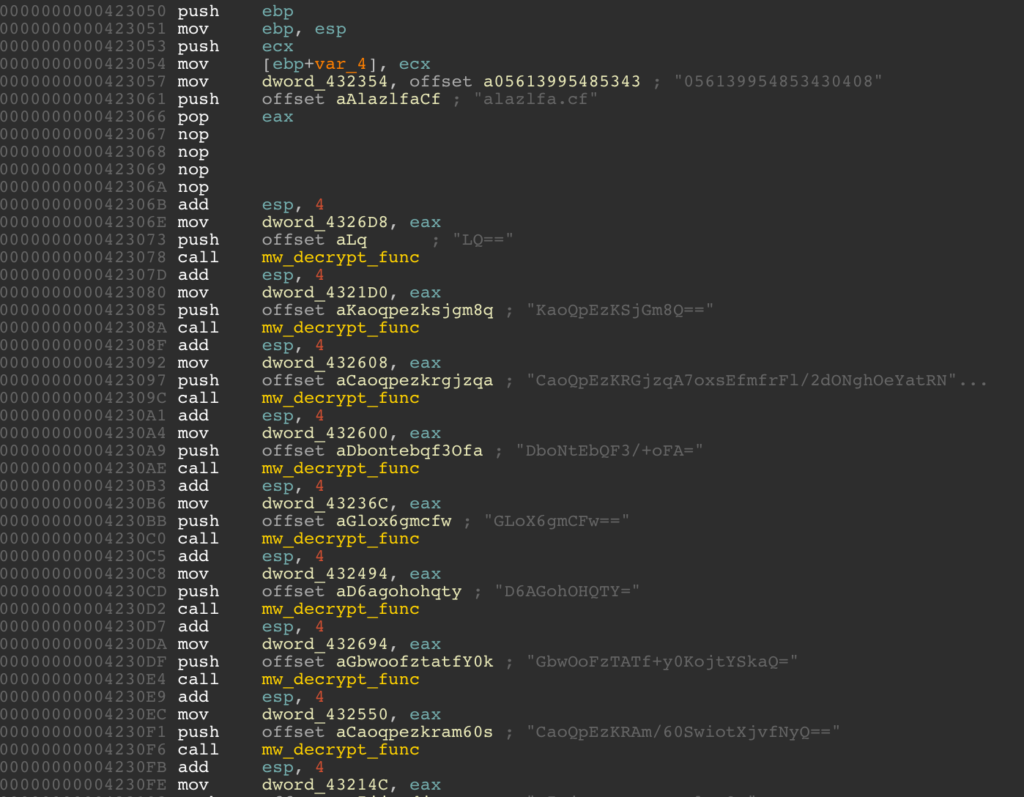
When looking at this function, I can see that it is a bit complicated with memory allocation and a lot of sub functions. Remember, we want to be lazy so we need to think of a better approach.
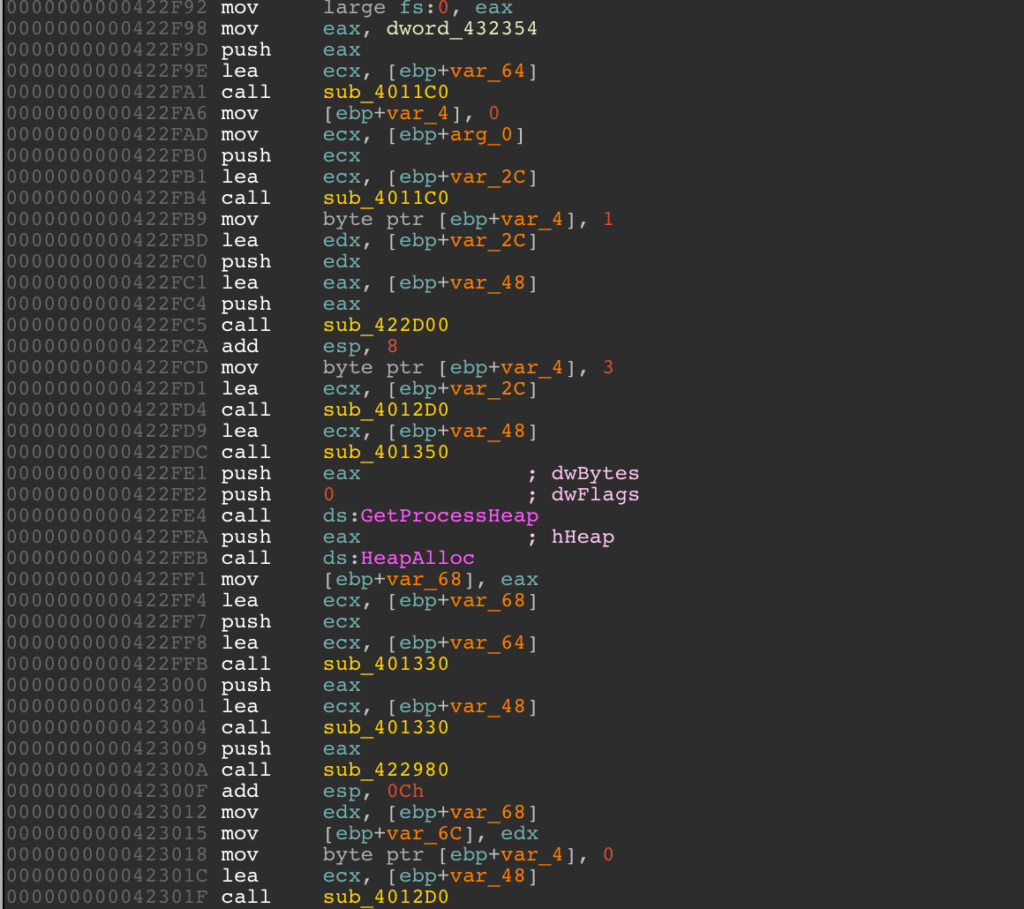
Emulation
I think that the decrypted string will be stored in eax after the function returns. So I will hook the return of one of the decryption routine and show rax to see if this is a unencrypted value.
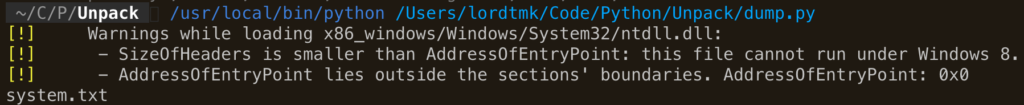
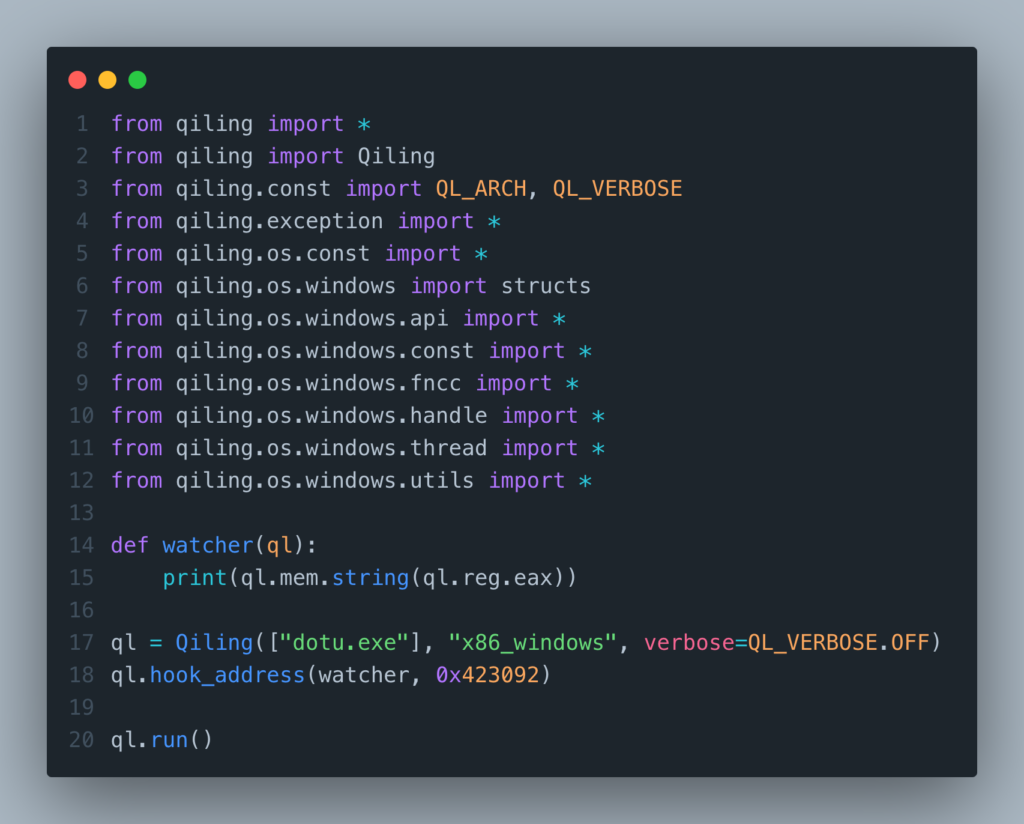
We can see that we have found the decrypted string. We now know that we must read all functions return value to get decrypted strings.
First, I gathered all the xrefs to the decryption routine with IDAPython and put them in a list. Their addresses are +0x8 which match with the return value address. Then, I simply run the binary and set up hooks on xrefs address, which will gather eax value and write a comment in IDA on the address.

Conclusion
As a said, I didn’t have much time on this challenge, so I decided to be as efficient as possible and explore other techniques to achieve the goals given. I must learn .NET to be able to understand and unpack programs. See you next week!
The script can be downloaded here :
https://github.com/lordtmk/Malware-Code/blob/main/oski_string_decryptor.py